Silicom Accelerated Crypto Adapter with NoLoad®: PQC Ready Cryptographic Acceleration

Integrate your CRM with other tools
Lorem ipsum dolor sit amet, consectetur adipiscing elit lobortis arcu enim urna adipiscing praesent velit viverra sit semper lorem eu cursus vel hendrerit elementum morbi curabitur etiam nibh justo, lorem aliquet donec sed sit mi dignissim at ante massa mattis.
- Neque sodales ut etiam sit amet nisl purus non tellus orci ac auctor
- Adipiscing elit ut aliquam purus sit amet viverra suspendisse potenti
- Mauris commodo quis imperdiet massa tincidunt nunc pulvinar
- Adipiscing elit ut aliquam purus sit amet viverra suspendisse potenti
How to connect your integrations to your CRM platform?
Vitae congue eu consequat ac felis placerat vestibulum lectus mauris ultrices cursus sit amet dictum sit amet justo donec enim diam porttitor lacus luctus accumsan tortor posuere praesent tristique magna sit amet purus gravida quis blandit turpis.

Techbit is the next-gen CRM platform designed for modern sales teams
At risus viverra adipiscing at in tellus integer feugiat nisl pretium fusce id velit ut tortor sagittis orci a scelerisque purus semper eget at lectus urna duis convallis. porta nibh venenatis cras sed felis eget neque laoreet suspendisse interdum consectetur libero id faucibus nisl donec pretium vulputate sapien nec sagittis aliquam nunc lobortis mattis aliquam faucibus purus in.
- Neque sodales ut etiam sit amet nisl purus non tellus orci ac auctor
- Adipiscing elit ut aliquam purus sit amet viverra suspendisse potenti venenatis
- Mauris commodo quis imperdiet massa at in tincidunt nunc pulvinar
- Adipiscing elit ut aliquam purus sit amet viverra suspendisse potenti consectetur
Why using the right CRM can make your team close more sales?
Nisi quis eleifend quam adipiscing vitae aliquet bibendum enim facilisis gravida neque. Velit euismod in pellentesque massa placerat volutpat lacus laoreet non curabitur gravida odio aenean sed adipiscing diam donec adipiscing tristique risus. amet est placerat.
“Nisi quis eleifend quam adipiscing vitae aliquet bibendum enim facilisis gravida neque velit euismod in pellentesque massa placerat.”
What other features would you like to see in our product?
Eget lorem dolor sed viverra ipsum nunc aliquet bibendum felis donec et odio pellentesque diam volutpat commodo sed egestas aliquam sem fringilla ut morbi tincidunt augue interdum velit euismod eu tincidunt tortor aliquam nulla facilisi aenean sed adipiscing diam donec adipiscing ut lectus arcu bibendum at varius vel pharetra nibh venenatis cras sed felis eget.
Silicom Accelerated Crypto Adapter with NoLoad®: PQC Ready Cryptographic Acceleration
I. Summary
The optimization of cryptographic processing is a critical requirement for modern high-performance computing, cloud infrastructure, and network security deployments. Fixed Function Application Specific Integrated Circuits (ASICs) such as Intel QuickAssist Technology (QAT) 1 and the Marvell Nitrox2 Security Processor have long served as a dominant baseline, accelerating established cryptographic standards such as TLS and IPsec. However, the advent of quantum computing necessitates a strategic re-evaluation of accelerator technology, moving the focus from optimizing the throughput of classical algorithms to ensuring long-term cryptographic agility.
Fixed Function ASIC’s continue to offer exceptional throughput for classical ciphers, but they present significant technical debt regarding Post-Quantum Cryptography (PQC) migration due to their inherent lack of agility. The Silicom Accelerated Crypto Adapter (SACA) 3,4, leveraging Eideticom’s NoLoad® Cryptography Acceleration Platform5, directly addresses this vulnerability by offering unparalleled reconfigurability and explicit support for emerging PQC standards, such as ML-KEM, ML-DSA, HQC and other emerging algorithms. And additionally, overall throughput performance can be similar or better compared to Fixed Function ASICS due to the ability of the FPGA platform to apply all its resources to a specific requirement.
Strategic deployment recommendations hinge on the organization’s tolerance for PQC risk and their refresh cycle planning. For High PQC readiness and flexibility the SACA/NoLoad solution is the superior choice, providing CPU independence and minimizing future hardware upgrade costs associated with PQC standardization shifts through crypto agility.
II. Flexible Acceleration via FPGA (Silicom Accelerated Crypto Adapter / Eideticom NoLoad)
A. Architecture and Core Technology
The foundational element of the SACA solution is the Altera FPGA, which allows for full algorithmic agility and dynamic reconfigurability. Unlike fixed ASICs, FPGAs enable enterprises to deploy, update, and optimize compute workloads, including complex cryptographic cores, without requiring physical hardware replacement.5
Eideticom’s NoLoad technology optimizes the data flow by utilizing a high-bandwidth, low-latency NVMe interface.5 This adoption of an industry-standard protocol, typically associated with fast storage, is a deliberate architectural decision to ensure efficient data movement between the host and the accelerator cores. Leveraging the NVMe protocol minimizes the potential I/O bottleneck often seen with traditional PCIe interfaces, ensuring that the sophisticated FPGA logic can operate at peak efficiency. The NVMe ecosystem also comes with the large administrative toolset for accessing telemetry, upgrading the firmware, and much more.
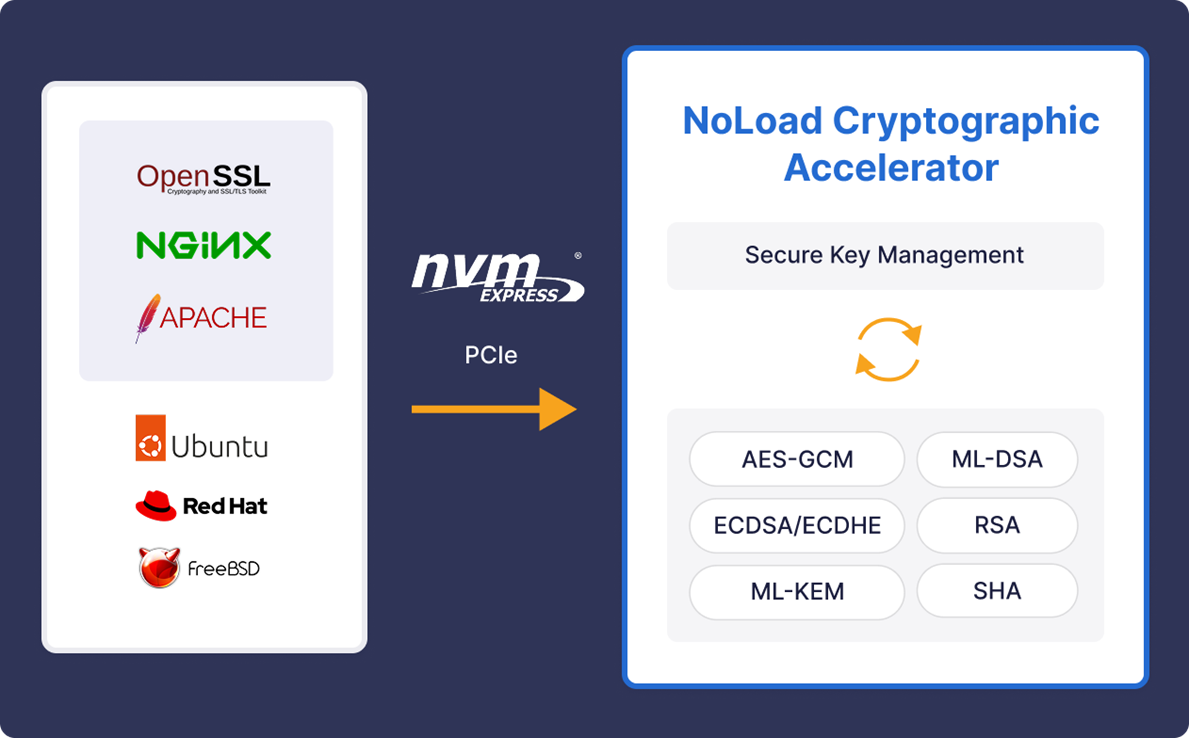
The NoLoad Cryptographic Accelerator platform includes TLS 1.3 support and direct integration into OpenSSL and other cryptographic software stacks, supports classical and PQC cryptography including NIST compliant ML-KEM (FIPS 203) and ML-DSA (FIPS 204). The platform also includes a True Random Number Generator (TRNG) and zero knowledge Secure Key Management for safely generating, storing and retiring cryptographic keys. Key Management can also provide ephemeral keys for ultra secure operations.
B. Silicom Accelerated Crypto Adapter (SACA) Implementation
SACA functions as a look-aside accelerator for cryptographic offloading and uses a PCIe X16 interface to deliver high throughput. A defining feature is its complete independence from the central processing unit (CPU). It ensures hardware-based acceleration without relying on any integrated CPU features. This means the acceleration benefits Intel, AMD, and ARM systems alike, strategically mitigating CPU vendor lock-in. This architectural freedom allows infrastructure architects to optimize CPU selection purely for application execution tasks, decoupling the compute roadmap from the security roadmap.
The SACA solution achieves seamless integration with mainstream applications through OpenSSL, NGINX, and Apache, allowing modern applications to offload computationally intensive operations without performance degradation.
C. Strategic Focus: Cryptographic Agility and PQC Readiness
The SACA/NoLoad solution is explicitly positioned to solve the challenges associated with PQC migration. It offers native support for essential Post-Quantum Cryptography algorithms, including:
- PQC Key Exchange: ML-KEM (Kyber) at 512, 768, and 1024 security levels.
- PQC Digital Signatures: ML-DSA (Dilithium) at 44, 65, and 87 security levels.
Furthermore, SACA supports Hybrid PQC schemes, such as Hybrid PQC X25519MLKEM768. Hybrid schemes are crucial for the transitional period, offering defense-in-depth by running both established classical ciphers and quantum-resistant algorithms concurrently.
The value of the SACA’s look-aside PCIe design becomes particularly pronounced in the context of PQC deployment as PQC algorithms are inherently computationally heavy.4 By isolating these complex operations onto a dedicated FPGA card, the SACA solution prevents PQC overhead from consuming scarce host CPU resources, a common issue when running these algorithms in software or relying on limited integrated accelerators.
The initial complexity and capital expenditure of FPGA solutions are generally higher than that of integrated ASIC solutions.17 However, this initial complexity cost is offset by the dramatic reduction in technical debt related to PQC migration. Since the SACA card can be updated via a firmware flash or IP core recompilation when PQC standards inevitably shift or require iterative updates, organizations avoid the severe cost of replacing underlying server hardware over multiple cryptographic lifecycles. This mechanism translates directly into superior TCO for long-term security deployments subject to evolving compliance requirements.
IV. Comparison: Fixed-Function vs. Agile Acceleration
The Intel QAT and Marvell Nitrox ASICs are optimized for maximizing throughput on known, established ciphers, providing proven speed-ups necessary for current high-volume TLS and IPsec workloads. However, the fixed-function architecture of ASICs means that if an organization must adapt to the mandatory shift to PQC, the cost of non-agility becomes prohibitive. ASICs require a full silicon refresh to implement major algorithmic changes, binding the security upgrade to the expensive and slow server hardware refresh cycle.9
The SACA/NoLoad solution, conversely, prioritizes algorithmic agility. While FPGAs historically carry higher initial complexity, their reconfigurability means that the hardware investment is protected against cryptographic obsolescence. For organizations with high PQC migration mandates, the investment in a flexible FPGA card minimizes the TCO associated with maintenance and compliance over the next decade.
C. Total Cost of Ownership (TCO) Analysis
TCO must account for direct costs (initial purchase) and indirect costs (staff time, maintenance, and future upgrade labor) over the solution's lifecycle.6
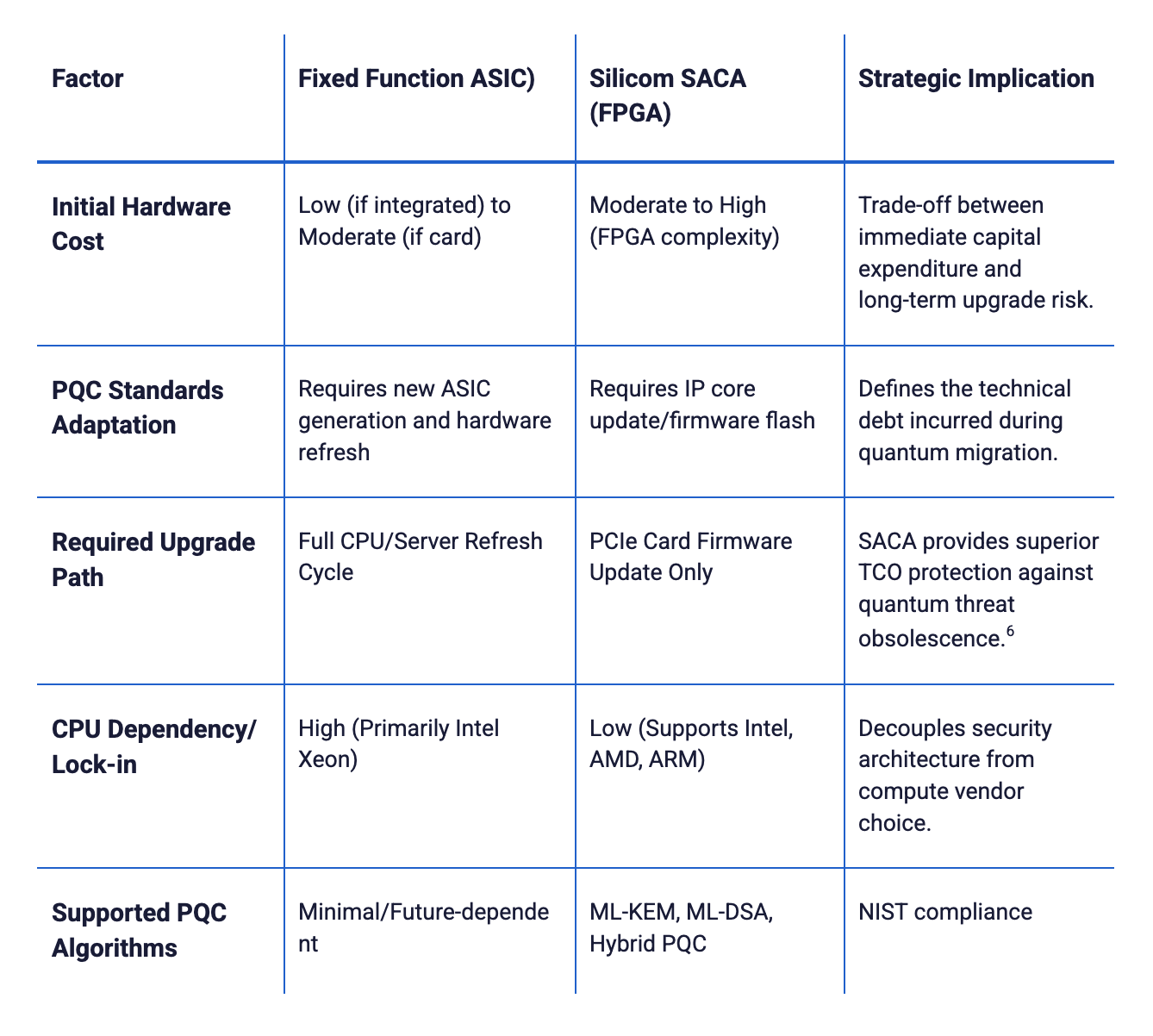
The crucial differentiator in TCO is the ability to decouple the compute roadmap from the security roadmap. By utilizing the CPU-independent SACA card, an organization can upgrade its cryptographic capabilities (via firmware update) without requiring a multi-million-dollar server refresh. This architectural freedom allows purchasing decisions for Intel, AMD, or ARM systems to be based strictly on application performance requirements, rather than being constrained by the availability of integrated acceleration features. For large-scale infrastructure facing mandatory PQC migration, this minimization of future hardware replacement costs constitutes a profound TCO advantage for the FPGA-based approach.
VII. Conclusions and Recommendations
The landscape of cryptographic offload technologies offers distinct architectural paths, each optimized for different strategic goals. While Fixed Function ASICs excel in providing maximum throughput for existing cryptographic standards with a mature software ecosystem, its fixed-function design presents a structural rigidity that significantly raises the long-term cost and complexity of futureproofing against quantum threats.
The Silicom Accelerated Crypto Adapter (SACA), utilizing Eideticom’s NoLoad FPGA technology, serves as the most strategic alternative to Fixed Function ASICs for organizations prioritizing cryptographic agility. Its reconfigurable architecture provides explicit, immediate support for PQC algorithms (ML-KEM, ML-DSA, HQC and others) and hybrid schemes, ensuring that the hardware investment is decoupled from the rapid evolution of security standards. This architectural choice minimizes the "cost of quantum resistance," leading to a superior long-term TCO compared to solutions requiring full hardware refreshes.
Citations
- What Is Intel® QuickAssist Technology, https://www.intel.com/content/www/us/en/products/docs/accelerator-engines/what-is-intel-qat.html
- Marvell Octeon TX2 Product Brief, https://www.marvell.com/content/dam/marvell/en/public-collateral/embedded-processors/marvell-infrastructure-processors-octeon-tx2-cn92xx-cn96xx-cn98xx-product-brief-2020-02.pdf
- Silicom Ltd. | The Silicom Accelerated Crypto Adapter - Silicom-USA, https://www.silicom-usa.com/solutions/fpga-based-solutions/ip-core-partners/the-silicom-accelerated-crypto-adapter/
- The Silicom Accelerated Crypto Adapter A Look-Aside PCIe Solution for Efficient Cryptographic Offloading, https://www.silicom.dk/wp-content/uploads/2025/05/Solution_Brief_SACA-1.pdf
- Unlock Efficiency with NoLoad Technology, https://www.eideticom.com/technology
- What is Cybersecurity TCO (Total Cost of Ownership)?, https://www.sentinelone.com/cybersecurity-101/cybersecurity/what-is-cybersecurity-tco-total-cost-of-ownership/



